Protecting Pharmaceutical Manufacturing Processes Against Cyber Threats
When it comes to pharmaceutical manufacturing, Industrial Control Systems (ICS) must function exactly as intended. Any unauthorized change to the manufacturing process, whether a malicious act or human error, can result in contaminated products, months of re-validations to resume production and heavy financial losses. Yet very little has been done so far to protect these critical industrial systems.
EXTERNAL/INTERNAL THREATS
Pharmaceutical companies are a primary target of industrial espionage. In most cases, cyber criminals are after intellectual property. However, a breach can easily lead to a wide range of operational disruptions, including downtime, production of inefficient drugs or poisonous drugs, spillage of hazardous materials and more.
Manufacturing companies report that their biggest concern is not necessarily external cyber-attacks, but rather insiders. Trusted employees, contractors and integrators who work on these complex, technologically intensive manufacturing processes can cause a wide range of disruptions, unintended outcomes and significant damage.
The leading threat, however, continues to be human error. Namely, unintentional mistakes. These are the leading cause of operational downtime. Simple errors like making changes to the wrong PLC, or incomplete maintenance to DCS systems, can cause of a wide range of disruptions and downtime, and result in unreliable products.
FDA REQUIREMENTS
The current good manufacturing practice (cGMP) regulations for validating pharmaceutical manufacturing require that drug products be produced with a high degree of assurance that they meet all the attributes they are intended to possess. The Food and Drug Administration issued guidance that requires manufacturers to maintain processes in a state of control over their entire lifecycle, even as materials, equipment, production environment, personnel and manufacturing procedures change.
Since drug manufacturing processes rely on ICS, these systems cannot experience any unintended changes. Therefore, all access to critical assets in these systems must be tracked, including PLCs and DCSs. However, ICS do not include built-in tools to enable automated tracking of access and changes. As a result, this requirement has been addressed using manual procedures, which are inaccurate and resource intensive.
LACK OF VISIBILITY AND CONTROL
Despite operating in a highly regulated environment, ICS networks used in pharma manufacturing lack basic controls required to ensure FDA requirements are being met. For example, most control devices such as PLCs, RTUs and DCS controllers lack authentication, use default passwords, and their communication is not encrypted. This makes it virtually impossible to prevent unauthorized changes to these systems. To make matters worse, the lack of event logs means it is very difficult to identify changes.
This lack of visibility and control prevents the early detection of incidents, whether caused by cyber-attacks or human error. As a result, problems are often detected too late - usually after disruptions have occurred and damaged goods are produced.
TRACKING ALL ICS CHANGES
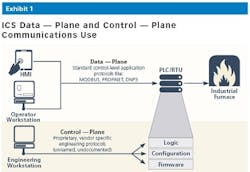
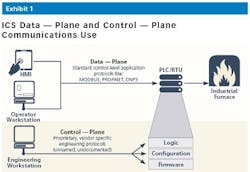
The primary security challenge in pharma manufacturing, like most industries, is visibility into engineering activities. In ICS networks, changes to control-logic, PLC firmware and configuration are executed over proprietary, vendor specific protocols known as the control-plane. Each OT vendor uses their own implementation of the IEC-61131 Standard for Programmable Controllers. These implementations are rarely documented, which in essence creates a “black box” syndrome.
Since changes to critical assets controlling manufacturing processes are executed using these proprietary vendor-specific protocols, there is no standard way to monitor/detect changes, whether malicious or unintentional mistakes, until it’s too late.
IT/OT CONVERGENCE
Since pharma products are manufactured using complex processes, there is increasing business value in connecting operational and IT systems. The ability to collect process and operational data plays an important role in meeting GMP and FDA drug manufacturing validation requirements. This is driving deeper integration between IT and operational networks.
With the efficiencies and cost savings provided by this blurring of the lines between IT and operational technologies, comes greater risk that external attackers can reach ICS through an IT network breach. A successful breach of the manufacturing network could result in unauthorized changes to control equipment (PLCs, RTUs, etc.) and operational disruptions or even the contamination of products.
WHAT CAN BE DONE
Monitoring all access and changes will provide the following benefits that both protect and improve the manufacturing process:
• Enables organizations to certify that no unauthorized changes were made to ICS and sensitive manufacturing processes.
• Early detection of suspicious and unauthorized access enables staff to respond and prevent, or at least minimize, disruptions and damage.
• Logging detailed information about each incident, whether legitimate or malicious, provides useful information about the who, what, when, where and how to quickly pinpoint the cause of the incident and shorten mitigation times.
• A comprehensive audit trail helps supervise the work of employees as well as third party integrators and contractors to ensure maintenance procedures and other work is performed on time and as planned.
• Reduces costs and resource investments associated with manual processes. Replacing them, instead, with more efficient and accurate automated processes. The integration of ICS and IT security monitoring can further reduce costs and improve incident handling.
The key to protecting your process comes in the monitoring of access and changes to manufacturing ICS infrastructure executed over control-plane protocols.
ABOUT THE AUTHOR
Barak Perelman is CEO of Indegy, an industrial cyber-security firm. Before founding Indegy, he led several multimillion dollar cybersecurity projects at the Israel Defense Forces. A graduate of the Talpiot military academy, Perelman has more than 15 years of hands-on experience in cybersecurity and protection of critical infrastructures.