In 2010, the industrial world changed, probably forever. The first cyber weapon, called Stuxnet, fashioned specifically to compromise industrial automation equipment was turned loose on the world of manufacturing. Stuxnet crossed the boundaries of IT infrastructure and moved into industrial automation. It, and soon-after other worms, compromised programmable logic controllers (PLCs), collected information on industrial systems and changed programming to deliberately damage the connected equipment. This was an alarm bell, but few managers had any idea of how to respond.
Today, process manufacturing in general and the pharmaceutical industry in particular are seeing increasing numbers of cybersecurity threats. To protect themselves, companies have to change the way they operate by addressing cybersecurity threats and designing appropriate defenses. Pharmaceutical companies have to recognize their high visibility and attractiveness as targets. They must work to understand cybersecurity concepts, identify weak points and implement appropriate security measures.
Process automation systems used to be considered safe. They were proprietary and isolated from external networks, effectively cutting off any attack vectors. This isolation didn’t last as companies established connections to IT networks to provide remote access by management. Often this provided a path all the way to the internet. Security-by-obscurity and air-gapped defenses quickly faded away due to a lack of effectiveness. The wide-scale introduction of the industrial internet of things (IIoT) is and its fully connected factory concepts is tearing down any remaining isolation protections.
No Single Cure-All Solution
A bank’s customers expect their money to be protected. Not only does it lock its vault and office doors to protect physical assets, it also has to protect customer data and financial information. These require different methods of protection, so a multifaceted defensive strategy is necessary. Similarly, a connected pharmaceutical operation must use appropriate methods to protect its physical and digital assets.
Different types of assets require different methods of protection and there should be multiple layers of protection. That’s the logic behind defense-in-depth security. It assumes any single layer of protection can and likely will be defeated, and thus uses multiple layers of protection. How these are conceived and implemented has to be driven with appropriate authority to be effective.
A Top-Down Approach
All companies make some type of security efforts from locking the office door to having a password on a computer. Companies large enough to have basic IT services will implement various cyber protections, inadequate though they may be. Such is not always the case for manufacturing systems, also called operational technology (OT). This is considered a different world and consequently treated differently. Security-by-obscurity concepts are often still used whether they are valid or not. Not all senior managers understand this second world or how to protect it, often resulting in insufficient resources and budgets.
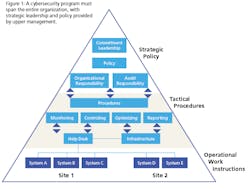
To secure the necessary support, a top-down approach is necessary, driven by senior-level managers using risk-based methodology. The strong upper management support must be supplemented by dedicated champions and defined funding under a clear implementation process. The top layers of the organization deal with strategy, risk and governance while lower levels deal with operational tasks (Figure 1).
Bottom-up approaches alone rarely succeed in the long term. They may help address point issues or specific weaknesses, but they can’t reach far enough to take the bigger picture and root causes into account. The preferred methodology is to align a top-down approach with its emphasis on planning with a bottom-up approach to the daily work that must be done to implement a sustainable cybersecurity program.
Conducting a Risk Assessment
A cybersecurity program extends far beyond installing firewalls and anti-virus software. Cybersecurity programs for the IT or OT domains should be embedded into the company’s business processes at multiple levels. One proven cyber security program methodology embraces the FARM approach:
- Frame—Defines scope
- Assess—Measures risks
- Respond—Outlines responses to threats, and
- Monitor—Ensure continued effectiveness.
The assessment step determines the current security and maturity level of the plant and OT networks. It derives baselines for the protections implemented in the response step, and maps any gaps against the industry’s and the individual company’s protection level.
Assessment Tools
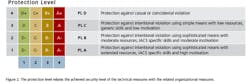
Protection level analysis provides a useful assessment yardstick. It is a two-sided technical measure to quantify the state of individual elements of a cybersecurity program. The protection level is derived from a combination of the security level, which can be provided by technical measures, and the existing maturity level of organizational measures. Let’s unpack this concept.
The security level (SL) is based on the requirements and represents the achieved protections available with the automation solution’s technical capabilities as determined by the assessment. The maturity level (ML) is inferred by the procedural capabilities of the plant or facility personnel. It is potentially associated with technical capabilities, such as administration of password policies enforced by automated login and account management software.
Consider an example: A small production unit is built around a bioreactor and its ancillary equipment. The process is controlled by a PLC programmed with the recipes and procedures to make the range of products produced in this bioreactor. When assessing this unit, it will be necessary to see how well protected the PLC is from threats coming through the plant network or other possible attack vectors. A low security level suggests it is very easy to extract information or reprogram the PLC. A high security level says it cannot be accessed without appropriate authorization, authentication, etc.
Maturity reflects more on how individuals understand company policies and interact with the control components and equipment. A low maturity score suggests sloppy practices such as writing the password for the PLC on the cabinet, or no password at all. A high maturity score indicates workers are methodical about following established procedures, and understand the importance of what they are doing and how their actions can support or hinder security efforts.
During the assessment process, security level and maturity level values are used as the axes of a four-by-four matrix, and a protection level value is assigned to each cell in the matrix. The protection level relates the achieved security level of the technical measures with the related organizational measures (Figure 2). Therefore, achieving a high protection level requires a high protection and maturity level.
Assessment Results
At the end of the cybersecurity risk assessment, the team produces a comprehensive risk assessment report, a threat catalog and a risk treatment plan. Based on the findings of this assessment, a security framework can be established along with policies and procedures. Policies are guiding principles for a variety of functions:
- Set direction in an organization
- Outline security roles and responsibilities
- Define the scope of information to be protected, and
- Provide a high-level description of the controls that must be in place to protect the OT domain
Policies make references to standards and guidelines. From a legal and compliance perspective, a policy is considered as a commitment from senior management to implement the program throughout the organization.
Standards help ensure security consistency across the business and the use of best practices. However, companies should be vigilant to ensure they do not become merely guidelines to be applied when convenient.
Procedures describe how each policy will be put into action in the organization, and describe how something is accomplished. Procedures describe who, what, where, when and why by means of establishing corporate accountability in support of a policy. The description is related to the work processes and not to specific technical solutions. The output of a procedure is an input to a work instruction describing how to perform a certain task, which is a more detailed portion of the procedure, and often solution- and role-specific.
Protecting Industrial Controls With the Right Tools
There are many different types of components, some visible or others behind-the-scenes, within an industrial automation system network. A typical pharmaceutical manufacturing setting involves multiple PLCs and distributed control systems (DCSes) controlling batch processing of various compounds.
The PLCs and DCSes control the low-level equipment: setting parameters, managing I/O, opening and closing valves, etc.
Let’s say the PLC running a process performs flawlessly 99 percent of the time. Those trying to understand and fix the 1 percent failure may assume there is something wrong with the process and waste much time trying to find the root cause. On the other hand, cybersecurity monitoring tools might recognize the failure was caused by a network incident resulting in a PLC misconfiguration, for example a network traffic jam caused a momentary bandwidth shortage resulting in dropped I/O commands.
Looking at such a situation from a cybersecurity perspective, a hacker aware of the incident might look for ways to replicate this issue by causing a domain name system (DNS) attack which would disrupt various processes, resulting in lost batches or worse.
Implementing Best Practices for Industrial Systems
A common problem today results from senior C-level managers trying to manage data security using tools and solutions designed for IT systems. They’ll direct the team to install firewalls, anti-virus tools and automated network patching. The CIO or other high-level executive can’t dive into the details of security risks in complex manufacturing environments. The IT and even OT networks may have sufficient cybersecurity protections, but not the PLCs and DCSs actually controlling the processes. The CIO might think everything is buttoned up because their anti-virus platform is up to date, but this often ignores the OT side.
Protecting the OT side often depends on a solution able to detect anomalies within industrial networks — a tool to monitor the PLCs and DCSes that aren’t part of the typical corporate data network. Armed with such a platform, engineers, control system operators and network security staff can have control over various threats without restricting the facility’s productivity or performance.
Ideally, such a solution continuously identifies and analyzes deviations from the norm, so a pharmaceutical manufacturer can eliminate risks to its IP and actual product integrity. Additional context and insights come from such a solution in terms of how it relates to other systems concurrently operating within the manufacturing plant. This type of solution gives meaning to the other system by providing guidance on what firewall rules should look like and sending alerts when firewall functions are out of baseline.
Managing the Security and Operational Sides
Some cybersecurity solutions only provide protections and insight for the network, but do not offer views into design flaws or misconfigurations within the actual production equipment. Returning to the 1 percent problem example with the PLC, an advanced industrial control monitoring solution provides this extra layer of insight so network managers can catch and stop small problems from becoming costly catastrophes.
The implementation of such a solution is critically important. When interfacing with the environment to create a monitoring point, the software will capture data from the network, but it must not create traffic itself. The solution is not hindering network communications, it is instead simply listening to the traffic and checking all of the proprietary systems and protocols. The objective is quick detection and remedies.
Even if a company can achieve an appropriate security level by introducing security measures into the different domains, the security level will decrease every day because new malware is constantly being created. Maintaining cybersecurity is a dynamic and never ends. It must be part of a sustainable security lifecycle supported by effective tools and constant reassessment.
[javascriptSnippet]